Enforce Your Application Security with Our Security for CI/CD Service
We offer security for CI/CD as a managed service, providing integration of security best practices and tools into the CI/CD pipeline.
Embedding application security measures is crucial for proactively detecting vulnerabilities in the early stages of the software development lifecycle.
Not only does it help to mitigate the risks of data breaches and cyberattacks, but integration of application security testing into the DevOps process facilitates faster delivery and ensures the application is secure and protected.
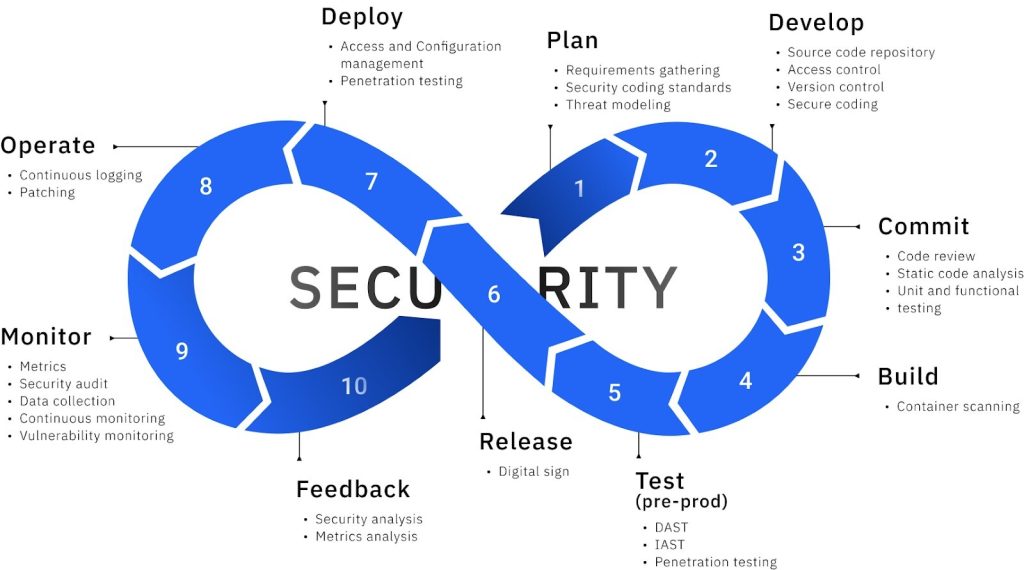
Customer Challenges We Help With
Non-secure deployments cause a delay in delivery and result in a longer time to market
What you get?
|
Insecure deployments not only lead to delays in the delivery process but also result in extended time to market. These security vulnerabilities, if not discovered at the early stage and addressed proactively, can introduce significant risks and potential setbacks into the overall development timeline.
The high cost of failures and security issues found in production
What you get?
|
Data breaches cost millions of dollars.
The high cost of failures and security issues identified in production can be detrimental to an organization’s bottom line and reputation. These issues often require emergency fixes, which can disrupt operations, lead to unplanned downtime, and result in additional expenses for incident response and recovery efforts. Moreover, the impact on customer trust and brand reputation can be long-lasting, potentially causing a loss of customers and revenue. To mitigate these risks and reduce costs, organizations are increasingly focusing on implementing robust security measures and comprehensive testing throughout the software development lifecycle to catch and resolve issues earlier in the process. This proactive approach not only helps prevent costly production failures but also contributes to a more secure and reliable software environment.
Lack of in-house expertise, knowledge, and skills around security
What you get?
|
Lack of in-house expertise, knowledge, and skills around security can indeed cause several issues for organizations, including: increased vulnerabilities, compliance and regulatory risks, data breaches and lost trust, operational disruption and missed business opportunities.
We have a team of skilled and experienced security professionals who can work closely with your in-house teams. They will provide training in security coding best practices and conduct thorough security assessments, vulnerability assessments, and penetration testing on your systems and applications, with findings that can be used to identify weaknesses and develop plans for remediation. Regarding investment in security tools and technologies that can automate security tasks and provide protection, we have strong experience in their integration, helping you to choose the appropriate tech for your unique needs.
What Do We Provide?
Our service will help your organization choose and integrate vulnerability scanning tools into the CI/CD pipeline.
- Continuous security testing through the integration of SAST, SCA, DAST, and IAST tools into the DevOps workflow
- Optimization of Continuous Integration and Continuous Delivery pipelines to meet security requirements
- Automated secure process of provisioning new IT infrastructure (IAC)
- Integration of runtime monitoring and the detection of vulnerabilities
- Implementation of CI/CD Access Controls and Secrets Management

Why is Security Testing Important?
Continuous security testing helps to enable end-to-end security and protect against data breaches, cyberattacks, and unauthorized access to sensitive information. Without a proper level of protection, a company can lose a lot of money and customer trust due to security breaches. Instead of fixing issues found in production, companies can save time and money detecting and remediating security issues as they occur and preventing them in production. The later a vulnerability is found, the more costly it will be.
Static Application Security Testing (SAST)
SAST
Static Application Security Testing (SAST) is a type of security testing performed on the source code or compiled version of an application to identify potential security vulnerabilities and coding errors, like SQL injection, cross-site scripting (XSS), and authentication flaws, allowing developers to fix them early.
Software Composition Analysis (SCA)
SCA
Software Composition Analysis (SCA) is the analysis of open-source components and libraries, examining an application’s dependencies, detecting outdated or insecure components, and providing actionable insights to remediate the identified issues. This is crucial because many security breaches result from exploiting vulnerabilities in third-party components.
Dynamic Application Security Testing (DAST)
DAST
Dynamic Application Security Testing (DAST) is a testing technique that evaluates the security of an application by interacting with it dynamically. It assesses the application while it is running to identify vulnerabilities and potential security weaknesses in real time.
Interactive Application Security Testing (IAST)
IAST
Interactive Application Security Testing is a technique that combines elements of both Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST).
In addition to the integration of security scanning tools, you can also conduct regular penetration testing events, which IBA Group provides as an additional service to evaluate and enhance your application security.
How Can Our Service Benefit Your Business?
Ensuring business continuity
Security measures integrated into DevOps processes help to prevent incidents and reduce risks of disruptions. This ensures that your business operations continue to run smoothly.Improving code quality
Static analysis tools review the source code for security issues before the application is deployed. This analysis identifies vulnerabilities like SQL injection, cross-site scripting (XSS), and authentication flaws, allowing developers to fix them early.Improving application security
The integration of security tools into the development and deployment process plays a crucial role in improving application security by identifying vulnerabilities, automating security checks, and providing actionable insights for remediation. This “shift left” approach catches security issues early in the development lifecycle, making them easier and cheaper to fix.Improve infrastructure security and management
Infrastructure as Code (IaC) helps to manage infrastructure through automation and enables a greater level of scalability and efficiency, but it may contain also errors in configuration and bring additional security gaps. The integration of IaC security scanning tools into CI/CD helps to detect and remediate errors and misconfiguration in infrastructure prior to code reaching production.![]()
Reduce risks
Comprehensive scans of applications, networks, and systems are performed regularly through the integration of security testing tools. These test various layers and components for vulnerabilities, helping to identify vulnerabilities and weaknesses in software and systems during testing and before malicious actors in production can exploit them.
Build trust
A dedicated focus on security practices increases confidence in the organization’s commitment to delivering secure and trustworthy software products, helping to build trust with stakeholders, retaining customers, attracting new ones, and fostering long-term relationships.Assisting organizations in any industry to embed security practices in the software development life cycle and enable the rapid development of secure applications
Our Expertise in Security
The Roadmap of Security for CI/CD Implementation Process
1 / Discovery
We start with analysis of your infrastructure and gather security requirements to determine what security measures are required. We will discuss your current CI/CD pipeline and analyze potential gaps in the process.
2 / Planning
Based on the analysis and collected requirements, we propose a plan to address your goals and expectations, create a roadmap. We also estimate the project schedule and costs.
We will choose appropriate security testing tools that best fit your needs and approve them with you.
3 / Implementation
With the plan in place, we start with infrastructure preparation and the implementation of a Proof-of-Concept (PoC). This involves integrating one of the tools to make sure that it fits the customer’s needs. After the PoC is successfully completed, we continue to integrate the selected tools (SAST/DAST/SCA/IAST, etc.) into the CI/CD pipeline in the test environment, as well as implementing log management and monitoring, dashboards, and more.
4 / Delivery
When the project scope is completed, we provide all artifacts and training on how to run automation and tools and how to use reports. We also offer recommendations for dealing with all the vulnerabilities found, including practical strategies for addressing them. Upon request, we can additionally offer continuous support to maintain the effectiveness and efficiency of the security testing process.
SUCCESS STORIES
To better understand how we roll, check out the stories of those who have already successfully worked with us.
BLOG
Get a better grasp from data warehouse provider expertise to make an informed data decision.
Why Work with Us
To summarize the points mentioned above, collaboration with us provides you with the following benefits:
- Security Audit of Your CI/CD Pipeline and Processes: comprehensive assessment to identify and address security vulnerabilities.
- Integration of Security Testing Tools into the CI/CD Pipeline: tailored integration of security testing tools, such as SAST, SCA, DAST, and IAST tools that align with your specific requirements.
- Integration of a Secret Management Solution: implementation of a robust solution for managing sensitive information.
- Centralized Monitoring of Application Vulnerabilities: access to a unified dashboard for monitoring and tracking all vulnerabilities within your application.
- Support and Consultation for Remediation Plans: guidance and assistance in developing effective remediation strategies to address identified vulnerabilities.
- Security Training for Your Employees: provision of training sessions to educate and empower your workforce in security best practices.
Working with us ensures a comprehensive approach to fortifying your CI/CD pipeline and processes, tailored to meet your unique needs while providing ongoing support, guidance, and training to enhance your overall security posture.

Contact us
Please fill in the form to get in touch with us and share your details. Feel free to provide any additional information or specific questions you might have. Our team is committed to responding promptly and thoroughly.Looking forward to hearing from you soon!








